Latest trends. Deep insights. Focused learning. Endless networking. CodeMonsters is the software development conference that offers it all. Come and learn how you can improve your knowledge and combine it with new technologies, to create monster-amazing code.
-
 17-19 OctoberSofia, Bulgaria
17-19 OctoberSofia, Bulgaria
Call for papers is now open!
Check out the conference schedule
CodeMonsters 2017 Speakers

Petyo Dimitrov
Musala Soft JSC
Petyo Dimitrov
Petyo Dimitrov is a software engineer with 10 years of working experience in various projects for international clients. Currently, he is a Software Architect at Musala Soft. His professional focus is in Java, Enterprise Application and Integration technologies, RESTful and XML Web Services and Service Oriented Architectures. He also enjoys sharing his experience and new technologies he is learning with colleagues at work, students at Technical University – Sofia and on different IT conferences in Bulgaria.
Enterprise Java developer’s survival guide
I have been working in the enterprise Java field for a while now and periodically friends and colleagues ask me for help and advice. Over time I have collected several of their questions and would like to share them together with my view and experience on the subject. Questions vary from how to choose between popular Java frameworks, benefits and drawbacks of using ORM, designing REST APIs, performance considerations, etc. Some of them are specific for the Java field, while others are general topics for enterprise applications.

Radi Palazov
DXC Technology
Radi Palazov
Radi Palazov is Director, Regional Delivery Center Bulgaria, Europe Commercial Delivery within DXC Technology. In this position, Radi manages over 1500 multi-technology professionals located in Sofia and Varna, delivering services globally to over 200 clients in Cloud, Workload, Platforms & ITO, Workplace & Mobility, Application Services, Cross Offering, Enterprise & Cloud Apps, Big Data & Analytics. In addition, Radi also acts as Cloud, Workload, Platforms & ITO Lead for Europe.
Prior to this, Radi was EU Restricted Build Center Leader in Project Delivery organization for Infrastructure Technology Outsourcing (ITO), within HPE’s Enterprise Services. In this role, Radi was accountable for delivering project portfolio services for EU Restricted business, from small, add-on requests, up through large transitions and transformations.
Further back, Radi was the head of Project Delivery in Sofia, leading a team of ~400 highly skilled specialists who delivered services in the Datacenter, Workplace, Project & Program Management domains. Back in time, Radi was the person who set up successfully the Network Services Tower in Sofia, part of the Global Delivery Center Bulgaria.
Radi brings 20+ years of experience in the field of IT. He holds multiple excellence awards for mature leadership and significant contribution to the strategic development of the Sofia ITO organization.
Mr. Palazov has a master’s degree in Computer and Information Sciences, and a diploma in Mathematics.

Daniela Kolarova
DXC Technology
Daniela Kolarova
Daniela Kolarova is a System architect at DXC Technology with more than 13 years experience with Java. She has worked on many international projects using Core Java, Java EE, Spring. Because of her interests in AI she worked on scientific projects at the Bulgarian Academy of Sciences and at Plovdiv University and did some presentations on AI conferences and a Java conference this years. She is a also a DZone Java and DZone AI contributor. Daniela Kolarova graduated “Informatics” at the Faculty of Mathematics and Informatics at Plovdiv University “Paisij Hilendarski“.
To Mock or To Stub? How to choose the right Design and Testing Approach?
The topic covers best practices and common mistakes developers experience while designing code and corresponding tests taking into account TDD approaches.

Petar Stanchev

Petar Stanchev
Petar Stanchev is currently Professor at Kettering University, Flint, Michigan, USA and Professor and Doctor of Mathematical Sciences at the Institute of Mathematics and Informatics at the Bulgarian Academy of Sciences. He has published 2 books, more than 200 chapters in monographs, magazines and conferences, over 200 conference papers and seminars.
His research interests are in the fields of semantics, image processing, multimedia databases, databases, information systems, expert systems, fuzzy sets and systems, decision making, e-commerce, web technologies, computer games.
He is currently editor-in-chief of two international magazines and a member of the editorial staff of several magazines. He is the Bulgarian representative in the European Commission’s OpenAIRE2020 project. He is the author of the first programming book in Bulgaria “I Program at Nine Years”. More details about him are on his page https://paws.kettering.edu/~pstanche/ .

Denis Danov
Dreamix Ltd
Denis Danov
Denis Danov is full-stack developer and dev lead at Dreamix Ltd. He has 5+ years of experience in software engineering, research and development. Denis has a Bachelor degree in Software Engineering from Sofia University and Masters degree in Embedded Systems. He has worked with many teams located all around the world to deliver successful products for international companies.
How to build Microservices Architecture with Spring Boot and Netflix Stack
The presentation will introduce the audience to the microservice architecture and how it is different from a monolithic one. It will focus on the different components that are necessary for a microservice architecture such as discovery service, configuration service, api gateway and others. For each one of the components will be highlighted why they are important for this type of architecture and how to implement them with Spring Boot and Netflix stack.

Steve Poole
IBM
Steve Poole
DevOps practitioner (what ever that means) leading a large team of engineers on developing, using, exploiting and evangelising cutting edge DevOps technology and practises across IBM
Long time IBM Java developer, leader and evangelist. I been working on IBM Java SDKs and JVMs since Java was less than 1. Also had time to work on other things including representing IBM on various JSRs, being a committer on various open source projects including ones at Apache, Eclipse and OpenJDK. Also member of the Adopt OpenJDK group championing community involement in OpenJDK. A seasoned speaker and regular presenter at JavaOne and other conferences on technical and software engineering topics.
The Anatomy of Java Vulnerabilities
Java is everywhere. According to Oracle it’s on 3 billion devices and counting. We also know that Java is one of the most popular vehicles for delivering malware. But that’s just the plugin right? Well maybe not. Java on the server can be just at risk as the client. In this talk we’ll cover all aspects of Java Vulnerabilities. We’ll explain why Java has this dubious reputation, what’s being done to address the issues and what you have to do to reduce your exposure. You’ll learn about Java vulnerabilities in general: how they are reported, managed and fixed as well as learning about the specifics of attack vectors and just what a ‘vulnerability’ actually is. With the continuing increase in cybercrime it’s time you knew how to defend your code. With examples and code this talk will help you become more effective in tacking security issues in Java.
Is the future of Java cloudy?
Java – it’s on billions of devices. We think it powers the world. Others disagree.
In this talk we’ll examine a few of the reasons why some developers believe Java is being left behind by younger (or at least different) programming languages. We’ll show where the claims make sense and debunk some of the more outrageous slander. We know the future of Java includes a more polyglot world so we’ll help you understand with practical advice where Java shines today and where you might be better using something else. We’ll also cover the challenges that all runtimes have in the new era of Cloud and how the Java community is leading the way in evolving Java into becoming the Cloud runtime of choice.
This talk will help you become more informed when dealing with those inevitable language cage fights around the water cooler. You’ll be able to refute the fake news and replace it with clear facts. Vote for Java – you know it makes sense.

Josh Long
Pivotal
Josh Long
Josh (@starbuxman) is the Spring Developer Advocate at Pivotal. Josh is a Java Champion, author of 5 books (including O’Reilly’s upcoming “Cloud Native Java: Designing Resilient Systems with Spring Boot, Spring Cloud, and Cloud Foundry”) and 3 best-selling video trainings (including “Building Microservices with Spring Boot Livelessons” w/ Phil Webb), and an open-source contributor (Spring Boot, Spring Integration, Spring Cloud, Activiti and Vaadin)

Marc Schettke

Marc Schettke
Marc Schettke is software engineer and consultant for embedded systems in the pro audio sector, with his main area of interest being real-time audio networks. He is using Rust since 2014 without regrets.
Concepts of Rust and how to apply them
A language that tracks resource lifetimes and has trait-based generics instead of garbage collection and mainstream object orientation – sounds weird? Rust takes a number of surprising or unfamiliar approaches to defy classic tradeoffs. In this talk innovative language features and idiomatic libraries of this emerging ecosystem are introduced and demonstrated with practical examples along with a glance at the project’s structure. While Rust admittedly demands a mindset different from mainstream languages, it could also reveal a new perspective on your code’s architecture – even in other languages.

Doychin Bondzhev
dSoft-Bulgaria
Doychin Bondzhev
Doychin Bondzhev has over 25 years of experience in the software and consultancy industries. For the last 17 years he is establishing his own business – dSoft-Bulgaria. During that time he utilized different technologies including CDI, EJB, Web Services, Swing, JavaFX, JSF, JAX-RS, JMS and also different databases and platforms. He used these technologies for business, banking, process control and other types of projects. Prior dSoft-Bulgaria, he was a senior developer at AtoZed Software, responsible for maintaining and developing IntraWeb for Win32, .NET and Java. He has a masters degree in computer science from Technical University, Sofia branch Plovdiv.
Making our day job easy by reducing boilerplate code using Project Lombok
Fed up of writing getters and setters? Or opening a big class and trying to find the important stuff inside, but feeling lost in the forest of boilerplate?
Project Lombok is an open source project that tries to help developers to get rid of as much as possible of that. It presents a set of annotations for different purposes. For example you can annotate your class/field with @Getter and lombok will generate for you getters for all your fields/field. @EqualsAndHashCode will help you by generating code for your equals and hashCode. And there are other annotations that help with other boring tasks.
In this presentation I will demonstrate how easy is to reduce the amount of code you have to write for some simple tasks using annotations provided by Project Lombok. I will explain how exactly works this technology. I will demonstrate how to add support for your annotated code in your favorite IDE so that you be able to use code completion and call methods that are not actually there in your source code.

Graham Charters
IBM
Graham Charters
Graham is an IBM Senior Technical Staff Member and WebSphere Applications Server Developer Advocacy Lead based at IBM’s R&D Laboratory in Hursley, UK. He takes a keen interest in emerging technologies and practices and in particular programming models. His past exploits include establishing and contributing to open source projects at PHP and Apache and participation in, and leading, industry standards at OASIS and the OSGi Alliance.
A first look at Open Liberty
Open Liberty is a newly Open Sourced, EPL licensed, Java application server. It supports the full Java EE and MicroProfile programming models and its lightweight, composable design makes it the ideal runtime for Cloud Native and Microservice-based applications. With the aid of demos, this session with take you through a first look at Open Liberty. Where to get started, core concepts, capabilities, how to install, configure, deploy, and more.

Cosmin Rentea
Adobe
Cosmin Rentea
Cosmin Rentea is a software engineer and trainer. His main interest lies in using Big Data technologies for innovative solutions, and his expertise is mainly in scalable backends, JVM, and microservices areas. He has an active presence in Bucharest JUG, local conferences, and workshops. He contributed to Big Data systems for digital marketing, enterprise solutions for large retail companies, and to Java and Go open-source projects.
Feature Flags – and using them wisely…
Feature flags (a.k.a. feature toggles) are a set of patterns that enable dev-teams to deliver features to users rapidly and safely.
This talk leads you on a journey with a dev team as they adopt feature flags, covering what they are, why they’re helpful, and how to use them successfully. Along the way, you’ll discover that feature-management covers a broader set of use cases than you might initially think.
We’ll see how different types of toggles can be categorized and learn why it’s important to manage the various types of toggles in different ways, even if they share a common underlying implementation. We will discuss different ways to store toggle configuration and enabling strategies, and how to prevent them from getting out of control.
As a practical demonstration, a real-life Java web application using an open-source solution (Togglz) will showcase how feature flags were employed while transitioning between its development stages.
Finally we’ll share best practices from the industry and tips on how to succeed with feature flags in the age of microservices.
Mutation Testing
How well tested is your system? How do you measure it? Code coverage can give you an answer, however how well are tests actually written, and… can we trust them?
As a developer: How do you know that even the smallest change to the code will make at least a test fail?
As someone with a management role: How do you handle big projects with high quality requirements, when developers can write a lot of unit tests which have no assertions whatsoever? (and yes, the test coverage is very high)
Mutation testing is a method to check the quality of your unit tests and show more reasonable and useful code coverage reports. This session will describe the main idea and concepts of mutation testing, and some technical means to implement it in Java/JVM.
Finally, a live example will follow, with the use of PIT Mutation Testing framework – first illustrating the concepts, and then showing results of testing a more complex Java web application.

Werner Keil

Werner Keil
Werner Keil has worked for more than 25 years as project manager, software architect, analyst and consultant on leading-edge technologies for Banking, Insurance, Telco/Mobile, Media and Public sector.
Among his earlier clients are Sony where Werner designed and implemented micro-format based tags for Sony Music.
He develops enterprise systems using Java, Java EE, Oracle or IBM, does Web design and development using Adobe, Ajax/JavaScript or dynamic languages like Ruby, PHP, etc.
Besides work for major companies he runs his own creative, talent and consulting agency Creative Arts & Technologies. In his spare time, he runs and supports open-source projects, writes song lyrics, novels, screenplays and technical articles. He is committing member of Eclipse Foundation, Apache Foundation and the Java Community Process, including his role as JSR-363 Spec Lead and Executive Committee Member.
Performance Monitoring for the Cloud
Performance Monitoring tools like Performance Co-Pilot (PCP) existed almost longer than the World Wide Web. It was developed in the early 90s by SGI. Parts were made available open source from 2000 on, which led to a further spread of the tool. In recent years an active community formed and a variety of new features and enhancements were added. PCP is now part of Red Hat and SuSE Linux Enterprise editions and included in many other Linux distributions. Versions for other Unix variants, OS X and Windows also exist. This session compares popular Open Source Monitoring Tools like Performance Co-Pilot, StatsD, Dropwizard Metrics, Prometeus and MicroProfile Metrics. How they each support Containers or Virtualization, share data with IT monitoring systems like Nagios or Zabbix, or process analyze and visualize it via Carbon, Graphite or Grafana/ElasticSerch.
Physikal – JSR 363 and Kotlin for Clean Energy
This session will give you a brief overview of how Tenkiv and Nexus Brain use Kotlin and Physikal/JSR 363 to calculate the optimal usage of alternate energy sources and control solar power systems used for making clean water anywhere from Flint Michigan to Afghanistan.
Java EE 8, MicroProfile and the future of Java EE

Wajdi Ben Rabah
SFEIR
Wajdi Ben Rabah
Wajdi Ben Rabah is a computer engineer specializing in mobile technologies (native and hybrid) and parallel realities. He has published articles around these subjects either on blogs or in print magazines. He was also a speaker at many international events. His main goal is to push the digital world forward via contributions on open source projects or via training sessions, workshops, conferences and meetups.

Pascal Hertleif
Rust
Pascal Hertleif
Pascal is a web developer by day and a passionate Rust enthusiast and evangelist by night.
Concepts of Rust and how to apply them
A language that tracks resource lifetimes and has trait-based generics instead of garbage collection and mainstream object orientation – sounds weird? Rust takes a number of surprising or unfamiliar approaches to defy classic tradeoffs. In this talk innovative language features and idiomatic libraries of this emerging ecosystem are introduced and demonstrated with practical examples along with a glance at the project’s structure. While Rust admittedly demands a mindset different from mainstream languages, it could also reveal a new perspective on your code’s architecture – even in other languages.

Stefan Judis
Contentful
Stefan Judis
Stefan started programming 6 years ago and quickly fell in love with web performance, new technologies, and automation.
He worked for several startups in Berlin and recently joined Contentful to tell the world how an API-first CMS can make you a bit happier.
He is also a curator of the web performance online resource Perf Tooling, organizer of the Web Performance Meetup Berlin, contributes to a variety of open source projects and enjoys sharing nerdy discoveries.
Decrease your conversion! Common ways to lock people out
Building products for the web means building products for everybody. We spend hours and hours on optimising user flows, tweaking designs and A/B testing the heck out of everything. The problem is that we as developers, product owners and designers often think about the targeted customer under optimal conditions and ignore minorities. In this talk, we will take a look at common problems of the web today and demonstrate how we can make it a more welcoming place.

Nakul Mishra

Nakul Mishra
Consultant around JVM and related technologies. Prefer automation over manual configurations. Keen on continuous delivery, unit testing and code simplicity. Interested in developing applications that requires creativity, imagination, fast-learning and zest for putting theory into code
Kotlin – boost your productivity
Kotlin came out as a result of pragmatic efforts, aimed to target problems encountered by developers during real-world tasks. It is an open-source industrial-strength language designed by JetBrains.
Thanks to “Full Java interoperability” it can blend easily in your Java projects. It means, from the day one you can start taking advantage of, the newly introduced language leveraging your java knowledge, use existing libraries and gradually evolve your code base to migrate to Kotlin.
In this talk, we will take a code-centric approach on how to get started with Kotlin; take a look on various features such as: null safety, smart cast, extension functions, data classes, let, etc. in order to improve code readability and maintainability.
We will also decompile some Kotlin code to get better understanding of what happens under the hood.
Last but not the least, we will build a demo application in Kotlin and backed via a spring-boot.

Andrzej Czarny
Ocado Technology
Andrzej Czarny
Andrzej Czarny is a Senior Software Engineer at Ocado Technology. His work is mostly focused on real time performance of warehouse control systems. He is involved in creating testing frameworks and Continuous Integrations for multiple teams. His main area of expertise is Java and concurrency.
A practical approach to Java Memory Model
Java Memory Model is an interesting area of multi-thread programming. It describes how threads interact through memory and what behaviours are allowed in concurrent execution. Most of java developers are familiar with mutual exclusion and synchronized keyword but sometimes we forget that beside mutual exclusion we also have to care about memory visibility.
The talk will introduce number of examples to help understand JMM. It will use OpenJDK Java Concurrency Stress tests framework (JCStress) to validate the results.

Stojan Peshov

Stojan Peshov
Stojan Peshov is Java developer with more than 12 years experience in web and back-end development. He has worked on a wide range of projects and business domains using open source libraries and frameworks such as Spring, Hibernate, Magnolia CMS, IceFaces, Hessian, RobotFramework, AngularJS, etc. As such, he has tasted different flavors of Java: JSP, JSF, JPA, JTA, CDI, as well as Test Automation, ETL, HTML5, Javascript and Web Services.
Post-Agile Methodologies and all that Jazz
It’s been 15 years since the Agile Manifesto was signed and several methodologies were raised ever since. There is almost no developer nowdays that haven’t adopted at least one of the Agile principles and uses them in everyday work or even private life. Some has even done improvised versions which work according their needs.
The question that’s been around these past years is if the Agile is old enough to become past and what’s the next big thing, is it a time to call it Post-Agilit period and what that means. What has or needs to change in order to abandon the old and become the Post Agilit followers.
Lots of teams already claim themselves as Post-Agility pioneers and some new ideas of methodologies have been introduced. I’ll try to bring an overview of some of them and bring you some thoughts that might help answering the above questions.

Dr. Pavlin Dobrev
Bosch Software Innovations
Dr. Pavlin Dobrev
Dr. Pavlin Dobrev is a Research and Development Manager at Bosch Software Innovations. The company owned by Bosch is focused on developing software for the Internet of Things (IoT). He is in charge of the entire support of ISO 9001, ISO 20000 and ISO 27001 at Bosch Software Innovations, as well as various research and customer projects.
Dr. Dobrev has almost two decades of experience in latest Java technologies, as well as in OSGi and embedded systems. He is an active participant in the OSGi Alliance, Java Community Process and other technical standards groups. He is a member of the Eclipse Foundation and participates in the development of the Eclipse IDE as a committer in the Equinox project.
Pavlin Dobrev has a PhD in Computer Systems in the area of Knowledge Management from the Institute for Parallel Processing, Bulgarian Academy of Sciences and holds an MsC in Computer Science from the Faculty of Mathematics and Informatics of Sofia University. He has written many scientific and technical publications and participated as speaker in prestigious international conferences.
Bosch IoT Suite – We Connect Everything
Bosch Software Innovations’ IoT platform allows you to realize innovative business models in the Internet of Things (IoT) and cross-domain applications. The Bosch IoT Suite is a flexible software platform based on open standards and open source. Its cloud services meet the requirements typical of IoT projects. Software developers can quickly set up prototype applications before implementing them, deploying them within minutes, and operating them at high availability.
In addition to the cloud services, the device management capabilities of the Bosch IoT Suite can also be used stand-alone and on premise. For the realization of gateway-based IoT scenarios our market-leading and OSGi-based ProSyst Gateway Software is ready to be used in different domains.
Part of the large CXP Group, PAC analyzed 14 companies in the field of IoT device management. The study looked at device management and IoT data integration for the comprehensive and centralized management of connected devices. In particular, it focused on cloud-based device management, the networking of a large number of different devices, and IoT data integration (iPaaS).
The PAC analysts rated Bosch Software Innovations as above average in several categories, noting in particular the company’s strong strategic focus on the Internet of Things.In addition, they designated the Bosch IoT Suite’s device management the leader in the European market and awarded it the “Best in Class” seal, thanks in part to the company’s strong references.
Both ProSyst Gateway Software and Bosch IoT Suite’s device management are developed from our team in Sofia.

Branko Tadic
IBM
Branko Tadic
Blanko Tadic is highly focused on business development and sales of IBM Bluemix Platform as a Service offering, including wide portfolio of cognitive Watson services, Big Data and predictive analytics services, API integration and security services, data platforms, cloud-native application design, development and publishing, scaleable cloud runtime platforms, internet of Things platform, Design Thinking methodology and prototyping and industry specific solutioning.

Doncho Minkov
Telerik Academy
Doncho Minkov
Doncho Minkov is one of the first trainers at Telerik Academy – a leading tech-ed organization in Bulgaria, grooming the next generation of digital builders. Throughout the years he has played a significant role in the continuous success of the Academy, helping the organization equip over 50K people with hands-on programming knowledge and in-demand digital skills. Doncho has over 10 years of experience in software development and IT trainings. The technologies he is currently most focused on include Java, Android, JavaScript and Node.js.
Asynchronous Programming in Android with ReactiveX
Creating a complex mobile application with multiple user interactions and asynchronous tasks and events, usually goes hand in hand with long lines of code that are difficult to comprehend and prone to errors. With ReactiveX, however, we can build slick apps for Android faster, easier and with less code. In this session, you will gain a good understanding of ReactiveX functional syntax and implementation. Through a live demo, you’ll also learn hands-on techniques and best practices you can use directly in your real world-projects.

Mitia Alexandrov
T-Systems
Mitia Alexandrov
Principal expert developer at T-Systems. Over a decade experience mainly in Java Enterprise, but interested in dynamic languages in JVM and experimental features. Open source contributor, blogger. Bulgarian Java User Group co-lead. Frequent conference speaker. jPrime/jProfessionals conference organizer.
Java on the GPU. Where are we now?
We will take a look at what actually a GPU is. In the beginning we will have a small introduction on how it evolved throughout the years. We will see how it can be utilized in the Java world. There will be a small intro to the world of OpenGL. And then we are going to move to CUDA and OpenCL technologies for general purpose massive computations on regular desktops or cloud machines. We will see what are the advantages and drawbacks, how can we easily use Java to utilize the GPUs in the cloud.
Java EE 8, MicroProfile and the future of Java EE

Andrew Lombardi
Mystic Coders
Andrew Lombardi
Andrew Lombardi is one of a new breed of businessmen: the enlightened entrepreneur. He has been writing code since he was a 5-year old, sitting at his dad’s knee at their Apple II computer. Having such a deep affinity for the computer model, it is no surprise that at the age of 17 he began to delve deeply into the inner workings of the human mind. He became a student of Neuro Linguistic Programming and other mind technologies, and then went on to study metaphysics. He is certified as an NLP Trainer, Master Hypnotherapist and Time Line Therapy practitioner.
Using all of his accumulated skills, at the age of 24, Andrew began his consulting business, Mystic Coders, LLC. Since the inception of Mystic in 2000, Andrew has been building the business and studying finance and economics as he stays on the cutting edge of computer technology.
Use Terraform to keep your infrastructure in sync
Terraform has changed the way many organizations deploy to the cloud. With a clear configuration language you can manage countless services (providers in Terraform) and ensure they are kept in sync with your deployment needs. Learn how to build out some of the most common patterns and infrastructures against AWS, and start writing your infrastructure as code today.

Petar Tahchiev
Nemesis Software
Petar Tahchiev
Petar Tahchiev (@ptahchiev) is a founder and CEO of Nemesis Software Ltd., a Bulgarian company which builds next-generation cloud-native e-commerce platform. He is a graduated award-winning mathematician from Bulgaria, who once worked as Jakarta Cactus lead developer at the Apache Software Foundation.
In 2010 he co-authored the best-selling second edition of “JUnit in Action”. Nowadays he is part of the Maven development team and is a regular speaker at some of the biggest open-source software conferences in the world – ApacheCON, JavaONE, SpringONE2GX, SpringIO, etc.
JUnit, Spring RESTDocs, Asciidoctor and Maven when you need to document your APIs
This presentation will focus on the challenges we faced when we tried to document our product – the Nemesis Ecommerce Platform. It will show you the different approaches we tried and why we actually decided to go for Asciidoctor and SpringRESTDocs. This presentation is not only a deep-dive into SpringRESTDocs functionalities, but it will also show you how we automated the whole process of documentation by extending SpringRESTDocs to produce our documentation widgets, specifically the rest-tester widget, how we let Maven pre-process all of that, and how we configured Asciidoctor to produce what is now our current documentation.

Radimir Bitsov
Project A Ventures
Radimir Bitsov
Radimir Bitsov is a front-end engineer with a passion for web performance, accessibility, and interface animation. He worked for several startups in Sofia and Berlin. Recently, he joined the Project A Ventures team. He loves the open source community and enjoys sharing techy discoveries.
How quick users think your site is — measure and speed up perceived performance
In this talk, I would like to demonstrate ways to speed up perceived performance and how we can measure it using the latest RUM (Real User Monitoring) metrics. The specific topics covered in this presentation will be how people sense time, techniques to achieve better performance perception in comparison to the actual expectation, synthetic monitoring vs. RUM, First Paint / First Contentful Paint (FP / FCP) using the Paint Timing API and Time To Interactive (TTI) via PerformanceObserver.

Anshuman Bhartiya

Anshuman Bhartiya
Anshuman Bhartiya has been in the IT industry for about 10 years and has had the opportunity to wear multiple hats. Anshuman has been a web developer, cloud consultant, systems engineer and security engineer to name a few. Anshuman has a varied skillset and he likes to tinker with the latest technology coming up with innovative solutions for difficult and challenging problems. Security, Automation and Innovation are some things he is really passionate about and he firmly believes in sharing knowledge and the Open Source community. You can find some of Anshuman’s work at his Github here.

Carlos Sanchez
CloudBees
Carlos Sanchez
Carlos Sanchez specializes in software automation, from build tools to Continuous Delivery. He has spoken at several conferences around the world, including ApacheCON, JavaOne, Fosdem,… Involved in Open Source for more than ten years, he is the author of the Jenkins Kubernetes plugin and a member of the Apache Software Foundation amongst other open source groups, contributing to several projects, such as Jenkins, Apache Maven, or Puppet. He works at CloudBees scaling the Jenkins platform.
Using Kubernetes for Continuous Integration and Continuous Delivery
Learn how to scale your Continuous Integration and Continuous Delivery environment using containers. The Kubernetes project provides a container orchestration solution that greatly simplifies app deployments in large clusters and you can use Jenkins and Kubernetes together to run jobs on-demand.
Building and testing is a great use case for containers, both due to the dynamic and isolation aspects, but it increases complexity when scaling to multiple nodes and clusters.
Jenkins is an example of an application that can take advantage of Kubernetes technology to run Continuous Integration and Continuous Delivery workloads. Jenkins and Kubernetes can be integrated to transparently use on demand containers to run build agents and jobs, and isolate job execution. It also supports CI/CD-as-code using Jenkins Pipelines and automated deployments to Kubernetes clusters. The presentation will allow a better understanding of how to use Jenkins on Kubernetes for container based, totally dynamic, large scale CI and CD.

Nikolas Burk
Graphcool
Nikolas Burk
Nikolas is a polyglot developer and GraphQL enthusiast. He graduated from university with a Master’s degree in Management of Information System and has worked as an iOS developer for bigger companies like SAP, smaller startups and as a freelancer. He loves to share his knowledge and has worked as an iOS Instructor at the Make School Product College in San Francisco before he joined Graphcool in January.
Building realtime apps with React & GraphQL Subscriptions
GraphQL is getting increasingly popular and many big companies like GitHub, Twitter and Shopify are already using it in production. In this talk, I want to demonstrate one of the newer and less-known GraphQL features: Realtime Subscriptions. After a quick introduction to the basics of GraphQL, we’ll build a realtime messenger app with React and Apollo Client. I’ll highlight the requirements for building a subscription server that works with Apollo and introduce best practices for implementing subscriptions on the frontend.

Roman Tsypuk
Lohika
Roman Tsypuk
Oracle Certified Java Expert. Contributes as a speaker on meet-ups, communities and conferences, mentors colleagues, has deep experience in telecom area and likes ham radio beyond programming. Roman is the most concentrated on topics about Spring, JVM performance, security, distributed systems, microservices and docker.
Organizer of Lohika’s Java community – weekly meetings with live coding session, new framework investigation, sharing experience.
Program committee member of morning@lohika community – monthly meet-up events for developers.
Test Driven Documentation with Spring Rest Docs
During this talk Roman will give a detailed overview of Spring Rest Docs as well as demonstrate practical usages of it within a Spring Boot app with live coding. We will discuss the tradeoffs that developer has if s/he uses swagger as base framework and what benefits spring rest docs provides. Also, Roman will advise how to migrate your existing swagger’s project documentation into asciidoc format, extend it with tests and start using Spring Rest Docs.
After this session you will be ready to apply Spring Rest Docs at any project – a new one from the scratch or on existing one.
Spring Rest Docs has provided robust, flexible approach that is called Test Driven Documentation. It extends well known Red-Green-Refactoring from TDD with additional phase of building documentation on the fly.
This approach aligns 3 main components in your project – code base, integration tests and documentation and you are absolutely sure that your documentation is always up to date because it is generated from your tests. Furthermore it supports HATEOAS and provides lots of new features that are not available in Swagger.

Brian Vermeer
Blue4IT
Brian Vermeer
Brian is a Software Engineer at the dutch company Blue4IT. He works mainly consultancy based on al sorts of java based project all over the country. His passion is in Java, (Pure) Functional Programming and Cybersecurity. Besides being an engineer he is a Reservist at the Royal Netherlands Air Force and a Taekwondo Teacher.

Itai Grady
Microsoft
Itai Grady
Itai Grady is an experienced Security Researcher in Microsoft. Previously, Itai was a member of various research and development teams for 15 years in several companies, including Aorato (acquired by Microsoft) and 8200 intelligence unit. Itai holds a B.Sc degree in Computer Science.
Here to stay: Gaining persistence by abusing advanced authentication mechanisms
Credentials have always served as a favorite target for advanced attackers, since these allow to efficiently traverse a network, without using any exploits.
Moreover, compromising the network might not be sufficient, as attackers strive to obtain persistence, which requires the use of advanced techniques to evade the security mechanisms installed along the way.
One of the challenges adversaries must face is: How to create threats that will continuously evade security mechanisms, and even if detected, ensure that control of the environment can be easily regained?
In this talk, we briefly mention some of the past techniques for gaining persistence in a network and discuss why they are insufficient nowadays. Followed by a comprehensive analysis of lesser known mechanisms, using non-mainstream methods.
We focus on how attackers may leverage various Active Directory features and authentication mechanisms (such as object manipulation, Kerberos delegation, etc.) to achieve persistence.
Finally, we show how defenders can secure their environment against such threats.

Alvaro Muñoz
Microfocus
Alvaro Muñoz
Alvaro Muñoz works as Principal Software Security Researcher with Microfocus, Software Security Research (SSR). His research focuses on different programming languages and web application frameworks searching for vulnerabilities or unsafe uses of APIs. Before joining the research team, he worked as an Application Security Consultant helping enterprises to deploy their application security programs. Muñoz has presented at many Security conferences including BlackHat, Defcon, RSA, AppSecEU, AppSecUSA, Protect, DISCCON, etc and holds several infosec certifications, including OSCP, GWAPT and CISSP, and is a proud member of int3pids CTF team. He blogs at http://www.pwntester.com.
Attacking .NET Serialization
2016 was the year of Java deserialization apocalypse. Although Java Deserialization attacks were known for years, the publication of the Apache Commons Collection Remote Code Execution (RCE from now on) gadget finally brought this forgotten vulnerability to the spotlight and motivated the community to start finding and fixing these issues. One of the most suggested solutions for avoiding Java deserialization issues was to move away from Java Deserialization altogether and use safer formats such as JSON.
.NET formatters such as BinaryFormatter and NetDataContractSerializer are known to share similar mechanics which make them potentially vulnerable to similar RCE attacks. However, the lack of RCE gadgets led some software vendors to not take this issue seriously as happened to Java before.
In this talk, we will analyze .NET serializers including third party JSON parsers for potential RCE vectors. We will demonstrate that RCE is also possible in .NET and present details about the serializers that are vulnerable to RCE by default and discuss common configurations that make other libraries vulnerable. We will try to generalize the attack techniques to other serialization formats and conclude with presenting several gadgets from system libraries that may be used to achieve RCE for the analyzed serializers. Finally, we will provide recommendations on how to determine if your code is vulnerable, provide remediation advice, and discuss alternative approaches.

Linda Naeun Lee
Tor Project
Linda Naeun Lee
Linda is a crypto evangelist that wants to improve secure software so that it’s easy for everyone to use. She currently leads the UX team at Tor Project. Inc, which acts as an internal service to other application teams to help with feature ideation, interface design, and user testing. She received her MS in Computer Science from the University of California Berkeley, where she researched the intersection of computer security and user research.
Call for action: help Tor with the battle against surveillance and censorship
This talk will give an introduction of the Tor Project and the current state of encryption/censorship battles. Come to this talk to learn about the different teams at Tor, what is currently being worked on, and what Tor needs help with. Join us in fighting for internet freedom!

Reza Rahman
CapTech Ventures, Inc.
Reza Rahman
Reza Rahman is a long time consultant now working at CapTech. He has been an official Java technologist at Oracle. He is the author of the popular book EJB 3 in Action. Reza has long been a frequent speaker at Java User Groups and conferences worldwide including JavaOne and Devoxx. He has been the lead for the Java EE track at JavaOne as well as a JavaOne Rock Star Speaker award recipient. Reza is an avid contributor to industry journals like JavaLobby/DZone and TheServerSide. He has been a member of the Java EE, EJB and JMS expert groups over the years. Reza implemented the EJB container for the Resin open source Java EE application server. He helps lead the Philadelphia Java User Group.
Reza has over a decade of experience with technology leadership, enterprise architecture, application development and consulting. He has been working with Java EE technology since its inception, developing on almost every major application platform ranging from Tomcat to JBoss, GlassFish, WebSphere and WebLogic. Reza has developed enterprise systems for well-known companies like eBay, Motorola, Comcast, Nokia, Prudential, Guardian Life, USAA, Independence Blue Cross, Anthem, CapitalOne and AAA using Java EE and Spring.
Master Class: Pragmatic Microservices with Java EE and WildFly Swarm (Part 1)
Master Class: Pragmatic Microservices with Java EE and WildFly Swarm (Part 2)
HTTP/2 and What it Means for the Java EE Ecosystem
Java EE 8, MicroProfile and the future of Java EE

Laszlo Boa
IBM
Laszlo Boa
Laszlo Boa is an IBM Cloud Architect (Bluemix) for Central and Eastern Europe at IBM.
IBM Cloud – quick application development with IBM Watson
IBM Cloud, Data and Cognitive point of view

Karolina Marzantowicz
IBM
Karolina Marzantowicz
Karolina bridges the technology, business innovation and psychology worlds. She acts as technical executive and a catalyst fostering curiosity to help lead the adaptation to rapidly changing IT environments and to drive organizational agility. Karolina has been supporting companies in driving complex digital transformations, building and executing high growth strategies, introducing emerging technologies, innovative products and services for global international brands as well as hacking growth with startups around the world.
Recognized in 2017, as one of top 20 Women in #fintech.
Karolina is guest speaker at global focus conferences, and universities; author of many publications and books.

Mladen Jovanovski
IBM
Mladen Jovanovski
Mladen Jovanovski is a Client Technical Specialist in IBM focused on both traditional data processing technologies and leveraging potential of new Big Data processing technologies. His main areas of expertise are overall solution architecture, data integration, storing data and subsequent data analysis in both on-premise and Cloud environments.
Master Class: IBM Watson Data platform elements
Data Science Experience, Data Catalogue, Data Pipelines
Data in the cloud – IBM Watson Data Platform – OS for Data Scientists
IBM Watson Data Platformis an integrated platform of tools, services and data that helps companies accelerate their shift to become data-driven organizations. It is the IBM public cloud foundation designed to support the data and analytics vision of whole enterprises, delivering a fully integrated platform that sustains both analytical investigations and putting insights into active use in production at any scale. It delivers the user experiences that amplify the ability of every data professional to execute on that vision, allowing teams such as data scientists, developers and business analysts to work together across different languages and data models.
IBM Watson Data Platform enables enterprises to:
- Connect to data of any kind, stored or streaming, cloud and on-premise, human created or IoT generated;
- Visualize, prepare and cleanse that data for use;
- Persist it in the most appropriate and cost effective scalable data stores (Object, noSQL, warehouse or transactional database) and catalog it for everyone to find and use;
- Analyze it in depth using projects, notebooks, machine learning models and more;
- Deploy the insights as compelling visualizations they can make decisions on, or baking them into existing or new applications, processes and more;

Siren Hofvander
Min Doktor
Siren Hofvander
Have you seen a fire breathing dragon dual wield my little pony figurines? How about an IT Security employee with a burning passion for keeping users safe, and security fun and accessible? Siren Hofvander delivers on the latter and strives for the former in her daily job as CSO for Min Doktor. She specialises in building security into the SLDC and firmly believes that security is a task for everyone, not just the hacker elite. She also heads up the Malmö based IT Security group SecuriTea and is an avid forum contributor.
Secure Session Management
We’re facing an increasing need for privacy and security when communicating between not only individuals around the world, but between systems as well. It is imperative that we secure our systems against intruders from the outside, but we must also compartmentalize and protect our systems from the inside.
- How do we build and maintain secure sessions for our users?
- What do we need to keep in mind when designing our systems?
- Which industry standards can you as developers apply to to your code to contribute to a more secure environment?
- And perhaps most importantly, what are the common mistakes we should learn from and try to avoid in the future?

Andres Cespedes Morales
Backbase
Andres Cespedes Morales
I’ve been working the last decade building Java enterprise applications for large companies and researching about new and trending topics on how to improve the way the software is made, especially focusing on REST web services and securing them. I’m MVB on Dzone, member of the Oracle JCP JSR 367, Auth0 Ambassador, and I’ve started my speaker career at my native city Medellin 2 years ago, currently, I’m working as a Consultant at Backbase and I’m always sharing thoughts and ideas on my website andrespedes.com, on medium as @andrespedes and on Twitter as well.
Mastering Spring Boot in 3 Simple Steps
Anyone can do some code snippets using Spring Boot, but to become a master at it is quite different. Spring Boot has become a de-facto standard for the Java development community due to out-of-the-box functionalities following a principle “convention over configuration”, this makes that many developers miss some necessary conventions to build more scalable, resilient and secure applications. You’ll learn how to tweak Spring Boot’s configuration, monitor and health check your app, extend Spring Boot and its available plugins, a simple way to secure your application with practical examples.

Marina Simakov
Microsoft
Marina Simakov
Marina Simakov is a security researcher at Microsoft, with a special interest in network security and authentication protocols.
She holds an M.Sc. in computer science, with several published articles, with a main area of expertise in graph theory. Previously spoke at BlueHat IL 2016 and DefCon 2017.
Here to stay: Gaining persistence by abusing advanced authentication mechanisms
Credentials have always served as a favorite target for advanced attackers, since these allow to efficiently traverse a network, without using any exploits.
Moreover, compromising the network might not be sufficient, as attackers strive to obtain persistence, which requires the use of advanced techniques to evade the security mechanisms installed along the way.
One of the challenges adversaries must face is: How to create threats that will continuously evade security mechanisms, and even if detected, ensure that control of the environment can be easily regained?
In this talk, we briefly mention some of the past techniques for gaining persistence in a network and discuss why they are insufficient nowadays. Followed by a comprehensive analysis of lesser known mechanisms, using non-mainstream methods.
We focus on how attackers may leverage various Active Directory features and authentication mechanisms (such as object manipulation, Kerberos delegation, etc.) to achieve persistence.
Finally, we show how defenders can secure their environment against such threats.

Nikolay Stoitsev
Uber
Nikolay Stoitsev
Nikolay Stoitsev is a software engineer at Uber where he is working on distributed systems handling payments. He is also a teaching assistant at Sofia University. He knows both what the CAP theorem is and how to center things with CSS.
Reusable patterns for scalable APIs running on Docker
The shipping containers were introduced around 1830s and since then they play a crucial role in the modern society by providing efficient packaging, storage and transportation. Today we see the same revolution happening in the DevOps world with the adoption of container technologies like Docker. They allow us to package, distribute and run software in a scalable and efficient way. In this talk we’ll see how we can abstract the common problem we solve everyday when building scalable Java APIs with Docker into design patterns to create reusable solutions. We’ll explore the good practices of writing Java applications with Docker. Then we’ll see how each design pattern can be applied in real scenarios that address different concerns that a large system creates. We’ll see some real life implementations of those patterns and how they help us solve problems in scalable systems. By the end of the talk we’ll have a very powerful abstraction to tackle the everyday problems we face in building big and impactful systems.

Michael Schrenk

Michael Schrenk
Michael Schrenk has developed software that collects and processes information for some of the biggest news agencies in Europe. Additionally, he has lectured at journalism conferences in Belgium, The Netherlands, and created several weekend workshops for The Centre for Investigative Journalism in London. Mike has also consulted on information security everywhere from Moscow to Silicon Valley, and most places in between. Along the way, he’s been interviewed by BBC, The Christian Science Monitor, National Public Radio, and many others. In addition to his interest in Journalism, Mike conducts a Competitive Intelligence consultancy in Las Vegas and is the author of “Webbots, Spiders, and Screen Scrapers” (San Francisco: No Starch Press, 2012). Michael Schrenk is also an eight-time speaker at the notorious DEF CON hacking conference.
Social Engineering the News
It might be called “Fake News” but it’s really social engineering at a massive scale. And since Fake News taints our information stream, it is also a breach of data integrity, which should be everyone’s concern. To make his point, Michael Schrenk explores the similarities between traditional social engineering and what has led to today’s Fake News epidemic. During this talk, you will learn how hackers use OPSEC (Operations Security) to plan successful social engineering attacks. Additionally, you’ll learn how information is weaponized, who’s making money with fake news, and how it influences decisions at a governmental level (even how countries go to war over false news stories). You’ll also explore techniques to guard against social engineering in your projects.

Ryan Cuprak
Dassault Systèmes
Ryan Cuprak
Ryan Cuprak is an CPG & Retail, Formulation R&D Development Senior Manager at Dassault Systèmes, co-authored EJB in Action 2nd Edition from Manning and the NetBeans Certification Guide from McGrall-Hill. He is also president of the Connecticut Java Users Group since 2003. Ryan is a JavaOne Rockstar Presenter. At Dassault Systèmes he works on the ENOVIA Enginuity chemical formulation software and is involved in desktop and backend server development as well as client data migrations. Prior to joining DS, Ryan worked for a distributed computing company, TurboWorx, and also Eastman Kodak’s Molecular imaging Systems group, now part of Burker. Ryan earned a BS in computer science and biology from Loyola University Chicago.
Preparing for Java 9 Modules
Java 9 has finally shipped! Will your application still work and are you ready for Java 9 modules? Java 9 modules (aka Project Jigsaw) is the biggest fundamental change to the Java runtime. Code that use Oracle/Sun private APIs will break. This session will cover the basics of Java 9 modules and also the current state of tooling. The ramifications to existing and legacy applications will be covered along with the steps you’ll need to take to harness the power of modules and write more maintainable systems.
Testing Enterprise Applications
Testing Java EE applications has never been easier. In this session, you will learn how to perform integration testing using Arquillian and Arquillian Cube. Unlike unit testing, integration testing enables you to test large segments of the application in the application container with minimal effort. You’ll see how you can test EJBs including MDBs and also mock key part of a system to test exception handling. In addition, technique for testing client-side JavaScript code with the backend server will be covered. Between Arquillian, Docker, and mocking, complete testability for Java EE is possible.
Java EE 8, MicroProfile and the future of Java EE

Svetlin Nakov
SoftUni
Svetlin Nakov
Svetlin Nakov has 15 years technical background as software engineer, software project manager, consultant, trainer, and entrepreneur with rich experience with the .NET and Java EE platforms, information systems, databases, Web development and software engineering. He is author of 7 books on computer programming and software technologies, C# and Java, and tens of technical and scientific publications. Svetlin has been a speaker at hundreds of conferences, seminars, courses and other trainings. He holds a PhD degree in computer science, medals from the International Informatics Olympiads (IOI) and the Bulgarian President’s award “John Atanassoff”. He has been a part-time lecturer in Sofia University, New Bulgarian University and the Technical University of Sofia. Currently Svetlin drives the largest training center for software engineers in Bulgaria – Software University where he teaches young people in computer science, software development and information technologies.

Andrew Krug
Mozilla
Andrew Krug
Andrew Krug is a Security Engineer for Mozilla Corporation working on Cloud Security and Identity and Access Management. Krug also works as a Cloud Security consultant and started the ThreatResponse project a toolkit for Amazon Web Services first responders. Krug has been a speaker at Black Hat USA, DerbyCon, and BSides PDX.
Automating Incident Response for AWS Compromises
Incident Response procedures differ in the cloud versus when performed in traditional, on-premise, environments. The cloud offers the ability to respond to an incident by programmatically collecting evidence and quarantining instances but with this programmatic ability comes the risk of a compromised API key. The risk of a compromised key can be mitigated but proper configuration and monitoring must be in place.
The talk discusses the paradigm of Incident Response in the cloud and introduces tools to automate the collection of forensic evidence of a compromised host. It highlights the need to properly configure an AWS environment and provides a tool to aid the configuration process.
Cloud IR How is it Different?
Incident response in the cloud is performed differently than when performed in on-premise systems. Specifically, in a cloud environment you can not walk up to the physical asset, clone the drive with a write-blocker, or perform any action that requires hands on time with the system in question. Incident response best practices advise following predefined practiced procedures when dealing with a security incident, but organizations moving infrastructure to the cloud may fail to realize the procedural differences in obtaining forensic evidence. Furthermore, while cloud providers produce documents on handling incident response in the cloud, these documents fail to address the newly released features or services that can aid incident response or help harden cloud infrastructure.

Steve Kosten
Cypress Data Defense
Steve Kosten
Steve Kosten is a Principal Security Consultant at Cypress Data Defense and an instructor for the SANS DEV541 Secure Coding in Java/JEE: Developing Defensible Applications course. He’s previously performed security work in the defense and financial sectors and led the security department for a financial services firm. At Cypress, Steve performs secure code review assessments, vulnerability assessment, penetration testing, and risk management reviews. He is also the Open Web Application Security Project (OWASP) Denver chapter leader, and presents security talks at various conferences. Steve holds a bachelor of science in Aerospace Engineering from the Pennsylvania State University and a Master of Science in Information Security from James Madison University. He currently maintains GSSP-JAVA, GWAPT, CISSP, and CISM certifications.
Secure DevOps: A Puma’s Tail
DevOps is changing the way that organizations design, build, deploy and operate online systems. Engineering teams are making hundreds, or even thousands, of changes per day, and traditional approaches to security are struggling to keep up. Security must be reinvented in a DevOps world and take advantage of the opportunities provided by continuous integration and delivery pipelines.
In this talk, we start with a case study of an organization trying to leverage the power of Continuous Integration (CI) and Continuous Delivery (CD) to improve their security posture. Then, we will focus on static analysis, how it fits into Secure DevOps, and introduce you to Puma Scan: a new open-source .NET static analysis tool. Live demonstrations will show Puma Scan identifying vulnerabilities inside Visual Studio and in a Jenkins continuous integration (CI) build pipeline. Attendees will walk away with a better understanding of how static analysis fits into DevOps and a .NET static analysis engine to help secure your organization’s applications.
Hacking the OWASP Top 10
Developers are always up against rigid deadlines, changing requirements, and constant production support issues. This leaves little time for keeping up with the current threats and defenses, and it inevitably makes security an afterthought. In this presentation, we will be discussing 4 of the vulnerabilities from the OWASP Top 10:
- A1: Injection
- A3: Cross-Site Scripting
- A4: Insecure Direct Object Reference
- A8: Cross-Site Request Forgery
After exploiting these vulnerabilities with a variety of tools (e.g. sqlmap, BeEF, and Burp Suite), we will demonstrate mitigation techniques to correct the vulnerability.

Ahmad Gohar
IBM
Ahmad Gohar
I am architect, a technical team leader,and IBM Certified Experienced IT Specialist with 9+ years experience in designing and developing enterprise solution using Oracle, IBM, and Open Source. I also have a solid technical and academic background, strong technical project management experience. I can also coordinate demos for QA team, perform code, design and test plan reviews.
Moreover, I hold M.SC In Software Engineering from Egypt, also MIBA in Global Business Management from ESLSCA France. I am also certified as OCEJPA, OCPWCD,OCPJP, OCPSQL/PL, OCASQL/PL, MCP. I Won 2014 Duke’s Choice Awards for eFinance.
Furthermore I am an Egyptian Java user group EGJUG member and EGJUG JCP group. My career has taken me to different companies such as eFinance, United Nations, ResalaSoft, Hyundai Construction, and Misr Consultant.
Enterprise Architecture for IT-Specialists and Architects, TOGAF as Example

Elaine Ou
Ethereum
Elaine Ou
Elaine is an engineer at Global Financial Access, a company that works on cryptographic integrity for smart contracts. She is a core developer for Ethereum Classic and contributor at Bloomberg View. Previously she was co-founder of Sand Hill Exchange, a Bitcoin bucket shop.

Subho Halder
AppKnox
Subho Halder
Subho Halder is the Co-Founder and CTO at Appknox, a mobile security company that helps developers and companies to build secure mobile application. He looks after the security technologies and the product development to ensure we are always ahead in our game. Subho has previously developed AFE (Android Framework for Exploitation) and has done in-depth research and analysis on mobile platforms. He has been also listed multiple number of times in various Hall Of Fame for finding out critical security vulnerabilities in Google, Apple, Facebook, Microsoft, and many more. He has presented many talks and conducted workshops at conferences like Black Hat, Defcon, ToorCon, SysCan, ClubHack, NullCon, OWASP AppSec, RSA Conference.

Javier Godinez
Intuit
Javier Godinez
Javier Godinez is a Principal Security Engineer, Red Team Founder and Software Developer at Intuit. He has been working in the Cloud security space for the last five years and has developed a number of applications for testing the security of Cloud deployments and patterns for operating in the Cloud securely. He has previously worked for SAIC and SSC San Diego delivering unique security platforms to support cybersecurity. Javier is a Certified Information Systems Security Professional (CISSP) and Certified AWS Solutions Architect.
Cumulus – A Cloud Exploitation Toolkit
There is a lack of tools for testing the security of Cloud deployments; The Cumulus Toolkit is an attack framework for exploiting the Cloud’s weak points. This talk covers AWS basics, IAM security, gaining a foothold and pivoting in the Cloud and demonstrates how to escalate privileges using the Cumulus toolkit.
The Cloud enables software projects to speed up development because it allows developers to provision infrastructure and make configuration changes to their networks without much friction. This ease of deployment was but a dream in the age of the traditional datacenter. However, the Cloud also brings new attack surface which needs further exploration. Cloud Identity and Access Management (IAM) services (such as Amazon’s) are primary targets for attackers as these typically control access to hundreds of API calls over many services.
Over the years there has been various discussions around cloud security, e.g., Pivoting in Amazon Clouds (2013), and few tools have been developed to enable testing the security of Cloud deployments. These tools are standalone, have not attained wide adoption, and/or have not made it into widely adopted toolkits. To fill this void, we have developed the Cumulus Toolkit. The Cumulus Toolkit is a Cloud exploitation toolkit based on the Metasploit Framework. We chose Metasploit because its wide adoption and its wealth of existing features.
The Cumulus toolkit is a set of modules and techniques that can be used perform privilege escalation, account takeover, and to launch unauthorized workloads. To illustrate security concerns resulting from lax IAM policies, we present the Create IAM User module which can be used to create a user with administrative privileges. To perform complete account takeover, an attack that we’ve seen in the wild, we present the User Locker module which is used to lock out all legitimate users out of the account. Finally, we present the Launch Instances module which can be used to launch Cloud hosts on demand.

Matt Raible
Okta
Matt Raible
Java Champion and Developer Advocate @okta with a passion for skiing, mtn biking, VWs, & good ?. Driving a ’66 21-window & a ’90 Syncro. Made in Montana.
Develop Hip APIs and Apps with Spring Boot and Angular
In this session, you’ll learn how to develop APIs with Java 8 and Spring Boot, then deploy them to the cloud. You’ll also learn how to develop apps with the latest version of Angular, make them work offline, and optimize them for production. I’ll show how to do this all with JHipster.
JHipster generates an application with Java 8, SQL or NoSQL databases, Spring profiles, Maven or Gradle, Webpack, WebSockets and BrowserSync. It also supports a number of different authentication mechanisms: classic session-based auth, OAuth 2.0, or JWT-based authentication. For production deployments, JHipster includes out-of-the-box support for AWS, Cloud Foundry, Heroku, as well as Docker and Kubernetes.

Aaron Cure
Puma Security
Aaron Cure
Aaron is a security consultant and an instructor and contributing author for the DEV544 Secure Coding in .NET course. After ten years in the U.S. Army as a Russian Linguist and a Satellite Repair Technician he worked as a database administrator and programmer on the Iridium project, with subsequent positions as a telecommunications consultant, senior programmer, and security consultant.
At Puma Security, Aaron focuses on developing security rules, as well as leading research efforts for data flow and taint analysis.
Aaron holds the GIAC GSSP-.NET, GWAPT, GPEN, GMOB, and CISSP certifications and is located in Arvada, CO. Outside the office Aaron enjoys boating, travel, and playing hockey.
Secure DevOps: A Puma’s Tail
DevOps is changing the way that organizations design, build, deploy and operate online systems. Engineering teams are making hundreds, or even thousands, of changes per day, and traditional approaches to security are struggling to keep up. Security must be reinvented in a DevOps world and take advantage of the opportunities provided by continuous integration and delivery pipelines.
In this talk, we start with a case study of an organization trying to leverage the power of Continuous Integration (CI) and Continuous Delivery (CD) to improve their security posture. Then, we will focus on static analysis, how it fits into Secure DevOps, and introduce you to Puma Scan: a new open-source .NET static analysis tool. Live demonstrations will show Puma Scan identifying vulnerabilities inside Visual Studio and in a Jenkins continuous integration (CI) build pipeline. Attendees will walk away with a better understanding of how static analysis fits into DevOps and a .NET static analysis engine to help secure your organization’s applications.
Hacking the OWASP Top 10
Developers are always up against rigid deadlines, changing requirements, and constant production support issues. This leaves little time for keeping up with the current threats and defenses, and it inevitably makes security an afterthought. In this presentation, we will be discussing 4 of the vulnerabilities from the OWASP Top 10:
- A1: Injection
- A3: Cross-Site Scripting
- A4: Insecure Direct Object Reference
- A8: Cross-Site Request Forgery
After exploiting these vulnerabilities with a variety of tools (e.g. sqlmap, BeEF, and Burp Suite), we will demonstrate mitigation techniques to correct the vulnerability.

Jack Shirazi
JavaPerformanceTuning
Jack Shirazi
Jack Shirazi is the founder of JavaPerformanceTuning.com and author of Java Performance Tuning (O’Reilly). He has published dozens of articles on Java performance related subjects as well as 10,000 performance tips over the years in his monthly newsletter. He was elected a Java Champion in the very first wave of elections in 2005 of people eligible outside Sun.
How to analyze the most common performance and memory problems in Java
The most common Java performance and memory problems, as reported by developers and operations staff over many surveys, have well understood analysis techniques. Here I’ll cover these with free tools and examples.
Featured Talks
Gaining persistence by abusing advanced authentication mechanisms
In this talk, we briefly mention some of the past techniques for gaining persistence, followed by an analysis of non-mainstream methods and focusing on leveraging Active Directory features to achieve persistence.
Identity theft: Developers are key
Identity theft is perhaps the most concerning kind of Cybercrime nowadays. It is not only about how secure is your program, but how aware are you? Or better said how naive are we in practice as developers in this big bad world.
Attacking .NET Serialization
In this talk, we will analyze .NET serializers for potential RCE vectors. We will demonstrate that RCE is also possible in .NET and present details about the vulnerable serializers and discuss common configurations that make other libraries vulnerable.
Automating Incident Response for AWS Compromises
Incident Response procedures differ in the cloud versus when performed in traditional, on-premise, environments. The cloud offers the ability to respond programmatically but what about a pwnd API key?
Into Ethereum
This talk will cover the inner workings of Ethereum and compare it with its more famous crypto cousin Bitcoin. How Ethereum works, how is that different than Bitcoin, Solidity, Smart Contracts in Ethereum and Bitcoin Script.
Secure Session Management
How do we build and maintain secure sessions? What to keep in mind while designing our systems? Which industry standards to apply for a more secure environment? What common mistakes to avoid?
CodeMonsters Highlights
A Unique Experience for Software Professionals
The first-of-its-kind and first-of-its-scale event for software engineers in Europe, which is focused not only on development technologies but is dedicated to improving every aspect of developers’ life.
Development Technologies & Latest Trends
Get ready to take in three days of the most popular and cutting edge development technologies combined with practical training, tips and tricks from the leading industry experts.
inspirational Speakers & Coding Tips
See our inspirational speakers dedicated to helping you reach the next level of coding and career development. Choose from more than 50 in-depth sessions, hands-on labs and discussions.
Engineering Culture & Soft Skills for Devs
Learn why a company’s engineering culture is possibly the most important thing an engineer can consider when evaluating a job offer and which are the most useful soft skills for software developers among other things.
Lifestyle & Free Time Activities
Get the chance to see new motorcycles and attend riding school, take cooking classes or try any other activity you would not expect to experience during a software development conference.
Community Friendly with Free Tracks
CodeMonsters is a commercial event, but we do support the community in any possible way. The conference offer free of charge tracks accessible through registration.
CodeMonsters Tracks
Core Languages
C/C++, JavaScript, Python, .NET/Mono, PHP, Ruby and Others
Emerging Languages
Go, Rust, Swift, Node.js
Modern Web
JavaScript frameworks & tools, CSS3, HTML5
Mobile Development
iOS, Android, Cross-platform frameworks
Databases
SQL, NoSQL, Distribution, Replication, Performance
Backend & HPC
Services frameworks and tools, Scaling, Performance Tuning, Algorithms
Big Data & Analytics
Data Storage, Processing, Analysis, Decision Making
QA Engineering
Continuous Integration, Automation, Verification
Cloud, DevOps & Infrastructure
The Operations perspective on Software Development
Development process, Methodologies, Tools
The healthy environment needed for every IT Professional
Security & Risk Management
Designing robust applications resilient to contemporary attacks
IoT and Robotics
RPi, Arduino, Embedded
Reserve your seat now
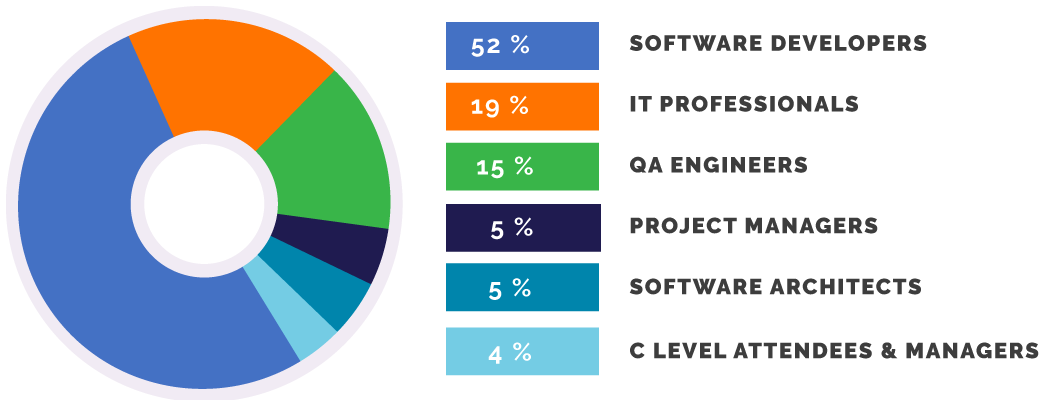
Who attends?
Highlights
60+ Speakers
5 Stages
80+ Sessions
1500+ Connections
Discussions
Networking
Still not convinced? See the most important reasons to attend.
Media Partners
See the full list of all attendee titles
Check pricing and packages
Venue
5000+ sq.m.
Innovative
Prestigious
Great location


Check out the conference venue
Latest news
The CodeMonsters Conference proved to be a huge success, with record attendances and expert speakers.…
With every purchase of a Professional pass you get full access to the international conferences…
As CodeMonsters is a must-attend software development event in Bulgaria supporting the community of software…
Registration for CodeMonsters 2017 is open! Register today to take advantage of Early Bird discounts,…
Check the agenda
Attending Managers from